Thursday, August 7, 2025
When Forced Authorization Codes Save Sales (And When They Don't): A Merchant's Risk Management Guide


When Forced Authorization Codes Save Sales (And When They Don't): A Merchant's Risk Management Guide
It's the busiest shopping day of the season, and your customer's card just got declined at the point of sale. They insist their account has funds, other customers are waiting in line, and you're facing a potential lost sale. This is when understanding forced authorization codes becomes crucial for your business.
A forced authorization code represents one of the most powerful yet risky tools in payment processing. When used correctly, it can rescue legitimate transactions from unnecessary declines. When misused, it opens the door to fraud losses that no merchant can afford. This comprehensive guide will help you navigate the complexities of forced authorizations, understand when they're appropriate, and most importantly, how to protect your business from sophisticated forced authorization scams that are increasingly targeting merchants.
What Are Forced Authorization Codes and How Do They Work?
A forced authorization code is a six-digit alphanumeric code provided by an issuing bank that allows merchants to override a declined transaction. Think of it as an emergency bypass key that lets you push through a payment when the standard authorization process hits a snag. These codes essentially tell your payment system to ignore the initial decline and process the transaction anyway.
The process works through a specific sequence of events. First, you attempt a standard transaction that gets declined. Next, you contact the issuing bank directly (never through the customer) to explain the situation. If the bank determines the decline was due to a soft issue like a technical glitch or AVS mismatch, they may provide you with a forced authorization code. You then enter this code into your POS terminal to complete the sale.
It's crucial to understand that forced authorization codes aren't magic numbers that guarantee payment. They simply override the technical decline at the point of sale. According to recent payment industry data, approximately 43% of merchants aren't fully compliant with PCI standards, making them particularly vulnerable to forced authorization fraud schemes.
Understanding Soft Declines vs. Hard Declines
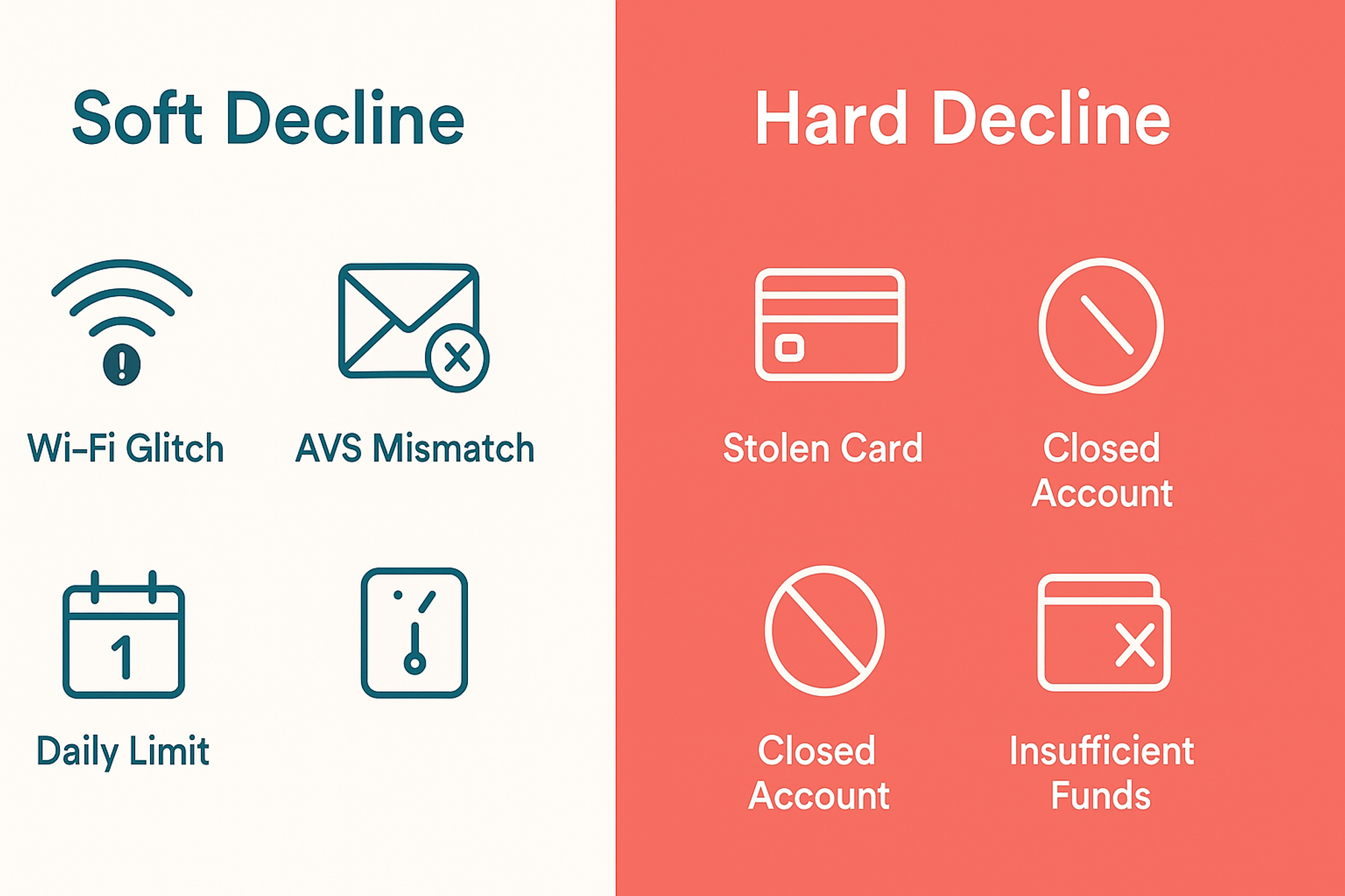
Not all payment declines are created equal, and understanding the difference between soft and hard declines is essential for proper forced authorization usage. Soft declines occur due to temporary issues that can often be resolved quickly – perhaps the customer entered their PIN incorrectly, your payment gateway experienced a momentary glitch, or there was an address verification mismatch.
Hard declines, on the other hand, represent permanent blocks on the transaction. These include situations where the card has been reported stolen, the account is closed, or there are insufficient funds. No amount of forced authorization can or should overcome a hard decline. Attempting to force through a hard decline not only violates payment processing agreements but also makes you liable for any resulting fraud or chargebacks.
The distinction matters because forced authorizations should only ever be attempted for soft declines. When you encounter a decline code indicating insufficient funds, suspected fraud, or a lost/stolen card, the only appropriate response is to ask for an alternative payment method. Understanding these decline codes can mean the difference between a saved sale and a costly chargeback.
When Forced Authorizations Are Legitimate
There are specific scenarios where requesting a forced authorization code makes business sense. Understanding these situations helps you make informed decisions that protect both your revenue and your customers' experience.
Technical Issues and System Glitches
Payment processing systems aren't perfect. Sometimes a customer's card gets declined due to technical problems that have nothing to do with their account status. Perhaps your internet connection dropped momentarily during the authorization request, or the issuing bank's systems experienced a temporary outage. In these cases, calling for a forced authorization can save a legitimate sale.
Address Verification Service (AVS) Mismatches
AVS mismatches are among the most common reasons for soft declines, especially for customers who have recently moved or are shipping to a different address than their billing address. While AVS is an important fraud prevention tool, legitimate customers can get caught in its net. A forced authorization might be appropriate here, but only after verifying the customer's identity through additional means.
Transaction Limit Exceedances
Some cardholders set daily transaction limits on their cards for security purposes. If a customer is making a large purchase that exceeds their self-imposed limit, they might need to contact their bank to temporarily raise it. In this scenario, the bank might provide a forced authorization code to allow the specific transaction while keeping the general limit in place for future protection.
International Transaction Blocks
Many banks automatically block international transactions as a fraud prevention measure. When legitimate international customers try to make purchases, their transactions might be declined even though their accounts are in good standing. After verification with the issuing bank, a forced authorization can complete these legitimate international sales.
According to 2024 payment fraud statistics, card-not-present fraud has dominated the fraud landscape, with 269 million card records posted on dark web platforms. This underscores the importance of careful verification before forcing any transaction.
The Risks: How Scammers Exploit Forced Authorizations
Understanding how criminals exploit forced authorization codes is your first line of defense against becoming a victim. Professional fraudsters have developed sophisticated methods to manipulate this system, and their tactics are constantly evolving.
The Fake Authorization Code Scam
Here's how the most common scam unfolds: A fraudster attempts a purchase with a stolen or closed account card. When it's declined, they act understanding and offer to call their bank themselves. They step away, pretend to make a call, and return with what they claim is an authorization code from their bank. The devastating truth? Any random six-digit number will work in most POS systems. Your terminal can't verify whether the code actually came from a bank.
This scam is particularly effective during busy periods when merchants are under pressure to move lines quickly. Fraudsters specifically target high-volume shopping days, knowing that harried staff members are more likely to accept their "helpful" offer to handle the bank call themselves.
Professional Fraud Rings
Beyond individual scammers, organized fraud rings run sophisticated operations involving multiple accomplices and sometimes even compromised merchant accounts. These operations often start with massive data breaches or identity theft schemes. The fraudsters harvest closed account numbers, then systematically attempt purchases at multiple locations, using fake authorization codes to push through transactions on dead accounts.
Some rings even recruit merchant insiders as accomplices, creating a particularly dangerous situation where the fraud originates from within the business itself. These inside jobs can result in massive losses before they're discovered, as the perpetrators know exactly how to exploit the system's weaknesses.
The Customer Service Exploitation
Another increasingly common tactic involves fraudsters who are exceptionally knowledgeable about payment processing procedures. They might claim to work in the payments industry themselves, using technical jargon to build credibility. They'll offer detailed explanations for why their card was declined and provide seemingly legitimate authorization codes, complete with fake reference numbers and timestamp details that make their story more believable.
Protecting Your Business: Best Practices for Forced Authorizations
Implementing robust procedures for handling forced authorizations isn't just good practice – it's essential for protecting your business from potentially devastating losses. Here's how to create a bulletproof system that allows legitimate forced authorizations while blocking fraud attempts.
Always Make the Call Yourself
The golden rule of forced authorizations: Never accept an authorization code provided by the customer. Always have your staff personally contact the issuing bank. This single practice eliminates the vast majority of forced authorization fraud attempts. Train your team to politely but firmly insist on making the call themselves, explaining that it's company policy designed to protect both the business and legitimate customers.
Implement Staff Training Protocols
Your employees are your first line of defense against forced authorization fraud. Comprehensive training should cover not just the technical aspects of processing forced authorizations, but also the psychological tactics fraudsters use. Teach staff to recognize red flags such as customers who seem overly familiar with payment processing terminology, those who insist on calling the bank themselves, or anyone who becomes aggressive when you insist on following proper procedures.
Regular role-playing exercises can help staff practice handling these situations confidently. Create scenarios where employees practice declining to accept customer-provided codes, identifying suspicious behavior, and following proper verification procedures even under pressure. PCI compliance standards emphasize the importance of ongoing staff training as a critical component of payment security.
Document Everything
Meticulous documentation protects your business in case of disputes or chargebacks. Record the decline code that triggered the forced authorization request, the name of the bank representative who provided the code, the exact time of the call, and any reference numbers provided. Take photos of the customer's ID if you're requesting additional verification for high-value transactions. This documentation becomes your evidence if you need to fight a chargeback later.
Set Transaction Limits
Establish clear policies about when forced authorizations are acceptable and when they're not. Many businesses set monetary limits – for example, no forced authorizations for transactions over $500. Others limit them to regular customers with established purchase histories. Whatever limits you set, ensure they're clearly communicated to all staff and consistently enforced.
Verify Customer Identity
For any forced authorization, especially on high-ticket items, require additional identification beyond just the payment card. Ask for a driver's license or passport, and compare the name and address to what's on file. For phone or online orders where you can't verify ID in person, consider requesting that customers send photos of their identification documents. While this might seem excessive, legitimate customers generally understand and appreciate the security measures.
Industry Regulations and Compliance Requirements
Understanding the regulatory landscape surrounding forced authorizations isn't optional – it's a critical component of risk management. Payment Card Industry Data Security Standards (PCI DSS) apply to every business that processes card payments, and forced authorizations fall squarely within their scope.
When you force a transaction, you're essentially taking full liability for that payment. If it turns out to be fraudulent, you can't claim you didn't know. The card networks are clear: merchants who process forced authorizations without proper verification bear complete responsibility for any resulting losses. This includes not just the transaction amount, but also any associated chargeback fees and penalties.
Your acquiring bank likely has specific requirements for forced authorizations outlined in your merchant agreement. These might include maximum transaction amounts, required documentation, or restrictions on certain types of businesses. Violating these terms could result in account termination, making it impossible for you to accept card payments at all.
Recent updates to payment regulations have made compliance even more critical. The shift to EMV chip cards was supposed to reduce fraud, but it's actually pushed more criminal activity into card-not-present transactions and authorization manipulation schemes. This means the stakes for proper forced authorization handling have never been higher. According to industry reports, businesses that maintain strong PCI compliance have significantly lower fraud rates and avoid the hefty fines associated with data breaches.
Technology Solutions for Safer Authorization Management
Modern payment technology offers sophisticated tools to help manage authorization requests more safely and efficiently. Understanding and implementing these solutions can dramatically reduce your fraud risk while maintaining a smooth customer experience.
Advanced Fraud Detection Systems
Contemporary fraud detection systems use machine learning algorithms to identify suspicious patterns in real-time. These systems can flag transactions that might warrant extra scrutiny before you even consider a forced authorization. They analyze factors like purchase history, geographic location, transaction velocity, and dozens of other variables to assign risk scores to each transaction.
Implementing these systems doesn't mean you'll never need forced authorizations, but they help you identify which situations genuinely warrant them. For instance, if your fraud detection system flags a transaction as high-risk and it's also declined by the issuer, that's a strong signal to avoid forcing it through.
Tokenization and Encryption
Payment tokenization replaces sensitive card data with unique tokens that are useless to fraudsters if intercepted. When combined with end-to-end encryption, these technologies ensure that even if criminals compromise your system, they can't access usable payment information. This is particularly important when handling forced authorizations, as you're already dealing with a higher-risk transaction.
Real-Time Authorization Monitoring
Some payment processors now offer real-time monitoring dashboards that show authorization patterns and flag anomalies. These tools can help you identify if your business is being targeted by fraudsters attempting to use fake authorization codes. For example, if you suddenly see multiple forced authorization attempts in a short period, that's a red flag that requires immediate investigation.
Automated Verification Systems
Newer POS systems can automatically verify certain types of information before allowing forced authorizations. They might check whether the authorization code format matches what's typically used by specific banks, or flag if the same code is being used multiple times. While not foolproof, these automated checks add another layer of protection against fraud.
Creating Your Forced Authorization Policy
Every business needs a written forced authorization policy that clearly outlines when these overrides are acceptable, who can authorize them, and what verification steps are required. This policy isn't just for your protection – it's a training tool for staff and a reference guide during high-pressure situations.
Start by defining your risk tolerance. How much potential loss can your business absorb if a forced authorization turns out to be fraudulent? This helps determine your transaction limits and verification requirements. A small retailer might set a $200 limit for forced authorizations, while a large electronics store might go higher but require manager approval and additional ID verification.
Your policy should specify exactly who can make the bank call for forced authorization codes. Ideally, limit this to managers or senior staff who have received comprehensive training. Include step-by-step procedures for making these calls, including what information to provide to the bank and what questions to ask.
Document your verification requirements clearly. Will you require photo ID for all forced authorizations, or only those above a certain amount? What about shipping addresses that don't match billing addresses? How will you handle phone orders where you can't physically verify the customer's identity? Each scenario needs clear guidelines.
Include escalation procedures for situations that don't fit neatly into your standard policy. If a long-time customer's card is declined for their typical purchase, how do you balance customer service with fraud prevention? Having predetermined escalation paths helps staff make consistent decisions even in unusual circumstances.
Your policy should also address the critical importance of avoiding authorization-related chargebacks. Make it clear that forcing a transaction after receiving a hard decline code will almost certainly result in a chargeback that you cannot win. The cost isn't just the transaction amount – it's also the chargeback fee, the time spent fighting it, and the potential impact on your chargeback ratio with your processor.
What to Do When Things Go Wrong
Despite your best efforts, you might still fall victim to forced authorization fraud. Knowing how to respond quickly and effectively can minimize your losses and help prevent future incidents.
Immediate Response Steps
The moment you suspect you've been defrauded through a fake authorization code, time is critical. Contact your payment processor immediately to report the incident. They might be able to stop the transaction from settling, though this window is usually very small. Document everything about the incident while details are fresh – the exact time, the amount, any security camera footage, and all interaction details with the fraudster.
File a police report even if you think it won't lead anywhere. This documentation is important for insurance claims and can help establish patterns if the fraudster targets other businesses in your area. Share information with other local merchants through business associations or online forums. Fraudsters often work specific geographic areas, and early warnings can prevent others from becoming victims.
Working with Your Processor
Your relationship with your payment processor becomes crucial when dealing with forced authorization fraud. Be completely transparent about what happened, including any procedural shortcuts your staff might have taken. Trying to hide mistakes usually backfires and can jeopardize your merchant account.
Most processors have fraud investigation departments that can help trace the fraudulent transaction and potentially identify patterns linking to other incidents. They might also be able to provide additional training resources or recommend technology solutions to prevent future fraud. Some processors offer insurance or protection programs for certain types of fraud losses – check if you're eligible and understand what's covered.
Learning from Incidents
Every fraud incident, successful or not, is a learning opportunity. Conduct a thorough post-incident review to identify what went wrong and how to prevent similar situations. Was it a training issue? Did staff feel pressured to bend the rules? Were your procedures unclear or difficult to follow in practice?
Use these insights to update your forced authorization policy and training programs. Share the lessons learned with all staff, not just those directly involved. Real-world examples are powerful teaching tools that help employees understand why following procedures is so important.
The Future of Payment Authorization
The payment processing landscape is evolving rapidly, and forced authorizations are likely to become less common as new technologies emerge. Understanding these trends helps you prepare for the future while managing current risks.
Biometric authentication is becoming increasingly sophisticated, with fingerprint and facial recognition already common on mobile payments. These technologies make it much harder for fraudsters to impersonate legitimate cardholders, potentially reducing the need for forced authorizations in situations where identity verification is the primary concern.
Artificial intelligence and machine learning are revolutionizing fraud detection, with systems becoming better at distinguishing between legitimate unusual transactions and actual fraud attempts. This means fewer false declines that might otherwise require forced authorization to complete legitimate sales. As payment security evolves, merchants who stay informed and adapt their procedures accordingly will be best positioned to balance sales opportunities with fraud prevention.
Real-time payment networks are also changing the authorization landscape. These systems provide instant confirmation of fund availability and account status, eliminating much of the ambiguity that currently necessitates forced authorizations. As these networks become more prevalent, the traditional authorization and settlement model may fundamentally change.
Conclusion: Balancing Risk and Opportunity
Forced authorization codes represent a double-edged sword in the payment processing world. Used correctly, they can save legitimate sales and improve customer satisfaction. Used carelessly, they open the door to significant fraud losses that can devastate a small business.
The key to successful forced authorization management lies in understanding the risks, implementing robust procedures, and maintaining unwavering discipline in following them. It's tempting to take shortcuts, especially during busy periods or with customers who seem trustworthy. But remember: fraudsters are counting on exactly that temptation.
As we've explored throughout this guide, the best practice for most businesses is to avoid forced authorizations whenever possible. The risks often outweigh the benefits, especially for smaller merchants who can't absorb fraud losses easily. When you must use them, follow every verification step religiously, document everything meticulously, and never accept authorization codes from customers.
The payment processing industry continues to evolve, with new technologies and regulations constantly changing the landscape. Staying informed about these changes, maintaining strong relationships with your payment processors, and investing in appropriate fraud prevention technologies are essential for long-term success.
Remember, every transaction carries risk, but forced authorizations amplify that risk significantly. By understanding when they're appropriate, how fraudsters exploit them, and what protective measures to implement, you can make informed decisions that protect your business while serving legitimate customers effectively.
Your approach to forced authorizations should be part of a comprehensive payment security strategy that includes regular monitoring of your authorization rates, staying current with PCI compliance requirements, and maintaining open communication with your payment processor about emerging fraud trends. In the end, the goal isn't just to process payments – it's to do so in a way that protects your business, your customers, and your reputation in an increasingly complex payment ecosystem.
FAQs About Forced Authorization Codes
Q: Can I force a transaction without calling the bank if the customer provides an authorization code? A: Never accept an authorization code provided by a customer. Always have your staff personally contact the issuing bank to obtain the code. Accepting customer-provided codes is one of the most common ways merchants fall victim to fraud.
Q: What's the difference between a forced authorization and a voice authorization? A: These terms are often used interchangeably. Both refer to manually obtaining an authorization code from the issuing bank when the standard electronic authorization fails. The key distinction is that both require direct merchant-to-bank communication.
Q: How long is a forced authorization code valid? A: Forced authorization codes are typically valid only for the specific transaction and amount for which they were issued. They should be used immediately and cannot be saved for future transactions.
Q: What happens if I process a transaction with a fake authorization code? A: You become fully liable for the transaction amount plus any associated chargeback fees. The transaction will likely be reversed when it's discovered to be fraudulent, and you cannot dispute this type of chargeback successfully.
Q: Should I use forced authorizations for online transactions? A: Forced authorizations for card-not-present transactions carry extremely high risk and are generally not recommended. Without the ability to verify the customer's identity in person, you have minimal protection against fraud.
Q: Can forced authorizations prevent chargebacks? A: No, forced authorizations do not prevent chargebacks. In fact, improperly forced transactions often result in chargebacks that you cannot win because you proceeded despite a decline.
Meta Description: Learn when forced authorization codes save sales vs. expose you to fraud. Expert guide covers legitimate uses, scam tactics, PCI compliance & risk management strategies.
Are you facing a chargeback?
You need a system. I can help.
Terms of sale
You need the right UI/UX
If your user inferface does not have the right verbiage, it is very hard to win. I will help you set yourself up for success.

Stipulated facts
You need to think like an attorney
If the customer did not dispute a fact, consider it admitted. You need to state the unstated. I will help you shape your case to state the facts most favorable to you.
Argue harm
You need a theory of the case
The best way to win a chargeback is to show how you were harmed. I will help you build a case that shows how the chargeback was against terms and hurt your business.

Sanity
You need to stop thinking about it
Chargebacks can feel like theft and business is already stressful enough. Having a proven system ready to go will save your sanity. Respond with confidence in minutes and move on with your day.